NFV (Network Function Virtualization) is a software process that carries many functions by using general-purpose hardware such as x86 and virtualization technology. Thereby reducing the cost of equipment expensive in the network. Through software and hardware decoupling and functional abstraction, network device functions are no longer dependent on dedicated hardware. Resources can be fully and flexibly shared, enabling rapid development and deployment of new services, and automatic deployment, elastic scaling, and fault isolation based on actual business requirements. And self-healing; these network functions can be On-demand mode, no need to install any new devices, such as operators can run virtual machines on x86 platform to perform open source software-based firewall functions without adding any new The same hardware facilities, such as CDN, NAT, DPI, VPN, IPTV, router, P-GW, IMS, etc., can be implemented by NFV-based software.
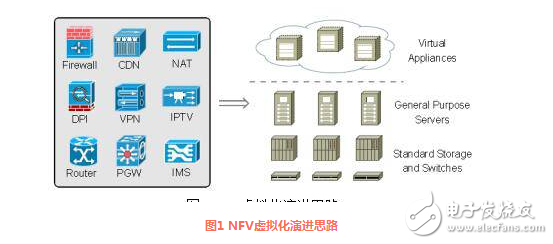
In the ETSI standard, a number of different scenarios are defined for the application of NFV, and the combination of the metropolitan area network mainly includes the following. Below we will analyze the five application modes of NFV under the domain network.
vRRIn the backbone network full-connection architecture, one or more pairs of routers are responsible for feeding back routing information to the entire network device. This is the route reflector (RR), which is generally used by the high-end core router of the dedicated hardware chip architecture. Since the primary function of the RR is to calculate routes rather than forwarding traffic, RR can be the first to migrate to the x86 architecture in a large backbone network, and it can adapt to changes and differences in user requirements more quickly. For example, changing the mechanism of the next hop of the BGP route, and introducing the comprehensive information such as the source address to perform routing, can implement the primary stage of load balancing of the backbone network traffic in an intelligent manner. At this stage, the high-end core router of the backbone network does not need to make any changes, and accepts the routing information reflected by the RR according to the traditional standard. So at this stage, it has extremely high implementation.
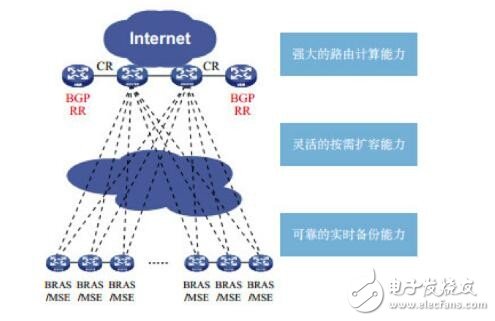
Figure 2 NFV in the metropolitan area network as an enhanced RR
The goal of operators introducing the RR of the x86 architecture is more than that. After the primary phase of the load balancing of the backbone network is deployed, the operator hopes to extract more traffic information from the existing backbone routers and collect the traffic information of the entire network by deploying the Controller. The Controller is optimized through comprehensive calculation and policy matching. Scheduling backbone network traffic to achieve ideal traffic engineering. Compared with the initial stage of RR x86 and protocol enhancement, the ideal target phase requires equipment upgrade or replacement of the existing network to support the relevant standard control protocol, and the standardization and improvement of the control protocol itself requires some time to accumulate.
vFWThe firewall needs to implement the isolation of the security domain in the traditional network environment, and also needs to implement the security domain in the virtualized environment (such as the production domain and its sub-areas, the supporting service domain and its sub-areas, the management domain and its sub-areas, DMZ). Isolation of domains and their sub-areas, etc.). For a security domain in a traditional network environment, a traditional firewall or a traditional deployment method may be used, and a security domain in a virtualized environment may be implemented by a virtualized firewall.
The traditional firewall is a kind of dedicated hardware, which supports virtualization inside the hardware firewall, which virtualizes one physical firewall into dozens, hundreds, or even thousands of independent logical firewalls. Each virtual firewall system can be viewed as a completely separate firewall device with independent system resources and the ability to implement most of the physical firewall functions. However, this is not the concept of NFV.
Using NFV technology, all the physical firewall's boards are converted into virtual machines. These virtual machines are installed on ordinary x86 servers and form a scalable and large-capacity firewall cluster through internal network communication. From a management point of view, the entire cluster is a very large-capacity firewall, which needs to have the following functions.
Rich network and security features to meet network security needs in enterprise branch and public cloud multi-tenant environments.
The control plane and the data plane are separated, and the multi-core data forwarding optimized for the virtual environment is utilized to make full use of computing resources.
The modular architecture and open network platform allow the network to run and control on demand, making it easier to implement NFV/SDN.
The physical network device adopts a unified software platform to provide the same functional features and a consistent management interface.
vDPIThe traditional way to deploy DPI is to embed DPI in various network devices, such as Session Border Controller (SBC), Traffic Detection Function (TDF), Gateway GPRS Support Node (GGSN), etc., as shown in Figure 3.
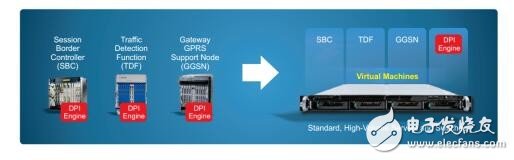
Figure 3 Traditional DPI deployment method
The main disadvantage of this approach is the high cost of implementing DPI technology multiple times on different hardware platforms. In addition, interworking between applications is difficult because each vendor may have a private way of performing DPI and presenting results. For example, a vendor might classify a stream as Twitter, but other vendors might use it as social media.
With SDN and NFV, DPI can be migrated from embedded network devices to become a shared feature hosted on a standard server (as shown in the right part of Figure 3). This approach reduces the total investment required for DPI because DPI only needs to be implemented on fewer machines (reducing fixed asset investment) and reducing energy consumption (reducing operating costs). In addition, interworking between different functions and DPI applications is less complicated, as it is relatively easier to implement a consistent format for application IDs and metadata. With SDN/NFV, DPI may no longer reside in an existing location.
vPOPOperators are thinking about the possibility of introducing x86, a higher computing power and a more standard and flexible hardware architecture, to the edge of the business of traditional metropolitan area networks. By deploying resource pools such as virtual CPE (vCPE), virtual BRAS (vBRAS), and virtual NAT (VCGN) under the x86 architecture, the user access control capability at the edge of the service can be flexibly expanded.
The operator first practices in the vCPE direction, and receives the aggregation node on the advanced function of the access gateway that was originally scattered in the user's home. Only the simplest Layer 2 access device needs to be deployed on the home side, which greatly reduces the client's investment. And maintenance costs.
The vCPE solution divides the traditional access gateway into two functional network elements, VG and PG, and weakens the PG function using proprietary hardware, which reduces the equipment procurement cost and subsequent upgrade requirements; the VG implementation that implements most network functions is based on The universal server's NFV technology implementation enables new functions and new services to be implemented without relying on hardware device updates, which can effectively control costs while greatly reducing TTR. NFV-based VGs can be deployed in the data center equipment room of the carrier to implement centralized management and maintenance of equipment and effectively reduce maintenance costs.
By receiving the operator data center equipment room on the egress gateway, the vCPE solution can better understand the user's business needs, integrate user consumption requirements and network provision capabilities, and introduce various value-added services to create new profit growth points. At the same time, operators can well grasp the user network operation behavior, provide real-time behavior analysis, ensure user network security, and meet various compliance requirements.
The application of vCPE can not only effectively reduce the network construction cost, but also reduce the maintenance cost through centralized deployment of the operator data center. At the same time, the user access function is realized through the cloud network service plane. In combination with the SDN technology, the service chain can also provide the IT office to the customer. Cloud, network security and other value-added services, the enterprise ICT application function is migrated to the operator's public cloud, and the user's on-demand access is realized through the SDN intelligent line to achieve the goal of cloud network integration.
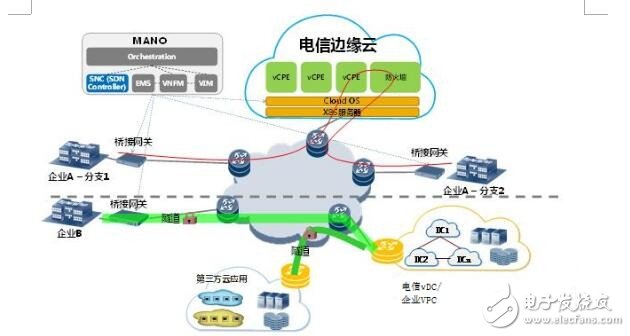
Figure 4 vCPE deployment mode
At the same time, BRAS and CGN are also trying to move towards x86. In the domestic operation of the mall domain network, BRAS is the most critical network equipment and role type. Building the metropolitan area network with the BRAS and its access network as modules, and continuously replicating the module expansion is the most typical mode. The network configuration of this mode is relatively fixed, and the network expansion of simple services can be well realized. However, there are also very obvious problems: each BRAS in the metropolitan area network is in a political position and cannot share resources. For example, in the place where users gather, only a few BRASs can be deployed, and some fiber links are connected from the access network to the BRAS room, so the utilization rate of the BRAS and the link is not high. Under the x86 architecture, BRAS and CGN are deployed as VNFs on standard servers. Standard servers can enhance computing and forwarding capabilities in a smooth and scalable manner, and can better adapt to L4-L7 service capabilities. A new vPOP is formed at the edge layer of the metropolitan area network (LAN), and various VNFs are deployed in a relatively centralized manner to form a resource pool. The resource pool can flexibly adjust resources for users and services, thereby improving the efficiency of the entire network. At the same time, the vPOP controller is deployed in the metropolitan area network to implement the functions of viewing, configuring, maintaining, and adjusting the resource status.
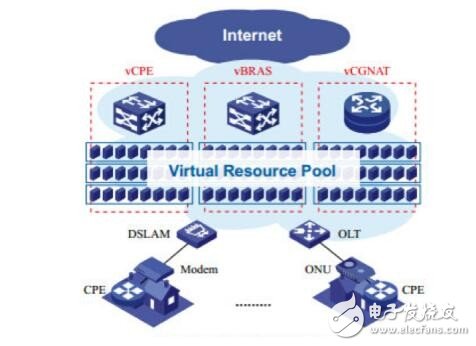
Figure 5 NFV application in metropolitan area network vPOP
For operators, vPOP is a new edge node for metropolitan area networks that can carry new business models. The telecom operators can not only provide differentiated value-added services to users based on their own business development, but also cooperate with third parties such as SPs and virtual operators to provide differentiated user experiences and further reflect the telecom operators in the Internet. The value of integration in the industry chain of the times.
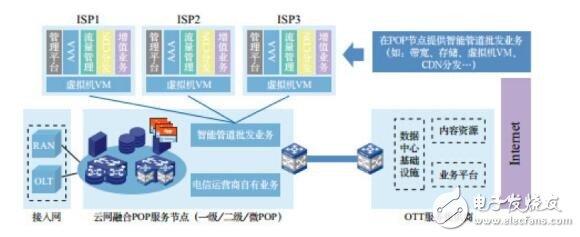
Figure 6 New business model brought by NFV application in metropolitan area network
As operators require complex technical verification mechanisms and decision-making processes, overall progress has been relatively slow. There are many types of large online devices for operators, and the traffic of large networks is not predictable. The network of the enterprise network/campus network is relatively closed, and the traffic model is relatively simple and has strong predictability. Therefore, it is relatively difficult to deploy SDN/NFV in an open network such as a carrier. However, operators have gradually introduced SDN/NFV into the network, and at the same time carried out a lot of pilot work.
In the enterprise network, a large number of VPN gateways can also be implemented by the NFV function. The most typical is the public cloud VPC service. By deploying firewalls and VPN gateways on x86-based virtual machines, the enterprise network is extended to the public cloud to provide unified network management for enterprises, including network configuration, security policies, and management strategies. Wait. Provide a consistent business experience by deploying QoS, WAN optimization, and more. This not only allows enterprise employees to access the public cloud securely and quickly through VPN, but also securely interconnects the enterprise public cloud and the private cloud at the second layer to achieve unified resource management, dynamic provisioning, flexible deployment and free migration.
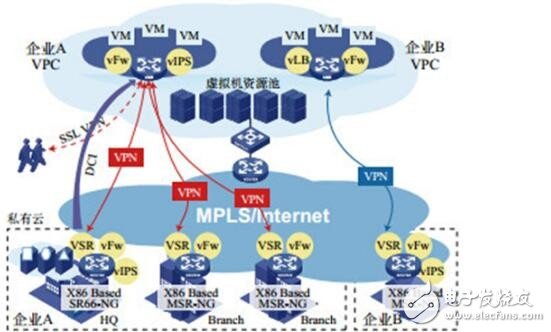
Figure 7 NFV application in data center multi-tenancy
In a survey of global CIOs by IDC, the most interesting of them in NFV services is SSL VPN (63.5%), followed by virtualization/cloud VPN (55.2%), cloud-based security. Web gateway (45.3%) and cloud-based IPSEC VPN gateway (43.2%).
From the perspective of CIO, NFV's service characteristics can be well adapted to the dispersed network landscape in the Asia-Pacific region. In addition, NFV enables enterprises to implement real-time activation and configuration of network services for branch networks in different locations through a unified online portal, eliminating the "one location, one device, one service" model.
At this stage, operators are mainly concerned with SD-WAN, operators can promote the sales of customers' multiple Layer 3 VPNs (for isolation), and provide enterprises with isolation and end-to-end network encryption. The integration of security and isolation is becoming a requirement in many industries, such as financial services and healthcare, to promote sales of government and corporate customers. According to the data, 54% of the 1,437 respondents considered deploying SD-WAN because of their low cost.
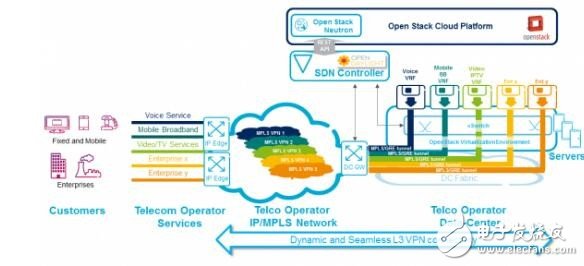
Figure 8 AT&T and Ericsson's SD-WAN solution
In the campus network, the concept of Openflow was first used for the experimental innovation of the campus network. At this stage, the campus network pays more attention to the Openflow switch and cloud platform products and solutions. The campus network solution needs to fully consider the compatibility and benefit of the existing network equipment and provide a smooth and evolved solution. At the device level, a dual plane is provided, so that the device can handle both traditional network services and SDN services. It can be combined with traditional networks or SDN networks to ensure smooth evolution. At the same time, at the protocol level, the Agent is recommended to be compatible with different Openflow protocol versions and compatible with different SBI protocol interfaces, so that devices can meet different protocol requirements and evolution requirements through simple software adaptation, and fully protect network investment.
vCDNCDN services are usually deployed at a location near the edge of the network.
Save to improve the quality of the user's business experience. Currently, CDN providers and operators use caching technology to provide users with such services using dedicated hardware. Since hardware resources are designed to be full at peak times, these cache resources are not fully utilized during most of the lifecycle. In the current deployment plan, the CDN nodes deployed by different service providers are independent, and the overall capacity is not used efficiently, especially for the tidal phenomenon, the utilization rate is very low.
With the popularity of end users, especially smart terminals, content-oriented content delivery has become the focus of business growth for network service providers. The dramatic increase in video traffic has put forward higher requirements for the user experience, and the CDN has risen. Using NFV technology on the CDN can be done for CDN controllers or for Cache. The Cache function is implemented by executing the relevant VNF ​​on the x86 general-purpose server in the data center adjacent to the end user side, thereby realizing efficient use of resources and ensuring user experience.
By utilizing and deploying NFV to implement virtualized caching, the underlying hardware resources can be combined and dynamically shared among CDN caches and other VNFs of multiple vendors, thereby effectively increasing the utilization of cache resources.
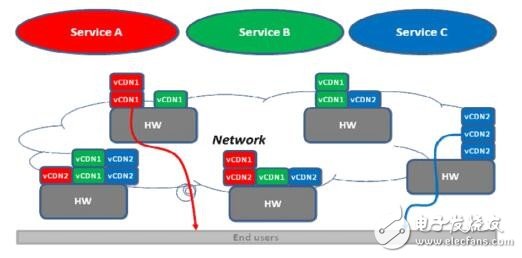
Figure 9 NFV application in the metropolitan area network vCDN
Low Voltage Static Synchronous Compensator
FGI`s FGSVG series low voltage dynamic reactive power compensation and harmonic devices are mainly composed of control panels, energy storage capacitors, reactors, IGBT, inverters, fuses and other devices. The low voltage Static Synchronous Compensator (STATCOM) has functions such as compensating reactive power, controlling harmonics, balancing negative sequence current and suppressing voltage flicker.
Svc Static Var Compensator,Low Voltage Synchronous Compensator,Low Voltage Static Compensator,Low Voltage Static Synchronous Compensator,Statcom Manufacturers,Power Quality Products
FGI SCIENCE AND TECHNOLOGY CO., LTD , https://www.fgi-tech.com
